1.0. Background
Chinese Advanced Persistent Threat (APT) actors constitute a substantial threat towards private and governmental entities from local to global levels. As contemporary geopolitical tensions in the Asia-Pacific region and beyond intensifies, so are the incentives for Chinese operations in cyberspace.
China’s APT network is a large web of intertwined actors capable of conducting sophisticated cyber operations against its opponents. While not every APT group is attributed to the Chinese government, Beijing is known to use APT actors to pursue its national interests. The United States (US) Office of the Director of National Intelligence 2021 Annual Threat Assessment states that China possesses substantial cyber capabilities and presents a considerable cyber threat towards digitised societies [source].
With target sectors primarily focusing on critical infrastructure objectives, hostile operations range from mere espionage activities to disruptions of high-developed systems with potential spillover to other actors in the supply chain. Hence, Chinese APT actors constitute a considerable threat to the ever-evolving digital attack surface.
While not an exhaustive list (at times, accessible information is very brief), this article aims to give a broad and, wherever possible, detailed description of known Chinese APT groups and how they correlate with China’s geostrategic aspirations.
1.1. Disclaimer
Attribution is a very complex issue. Groups often change their toolsets or exchange them with other groups. Therefore, be aware that information published here may quickly need to be updated or altered based on evolving information. Moreover, cyber security companies and Antivirus vendors use different names for the same threat actors and often refer to the reports and group names of each other. However, it is difficult to keep track of the different terms and naming schemes, but below are additional lists of known alternative names for each group.
1.2. Terminology
APT: “An APT uses continuous, clandestine, and sophisticated hacking techniques to gain access to a system and remain inside for a prolonged period, with potentially destructive consequences” [source].
Phishing: Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers [source].
Spear phishing: Spear phishing is an email or electronic communications scam targeting a specific individual, organisation or business [source].
Zero-day: A zero-day vulnerability is an unknown exploit that exposes a vulnerability in software or hardware and can create complicated problems before anyone realises something is wrong [source].
Supply chain: A digital supply chain is a set of processes that use advanced technologies and better insights into the functions of each stakeholder along the chain to let each participant make better decisions about the sources of materials they need, the demand for their products and all of the relationship in between [source].
Trojan: A Trojan is a malicious program downloaded and installed on a computer that appears harmless [source].
1.3. The Expanding Digital Attack Surface
The digital attack surface refers to “the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from, that system, system element, or environment” [source].
Increasing interconnectedness enhances potential entry points and vulnerabilities towards unauthorised access to protected systems. Developed countries depend on broad domestic and foreign networks of digital solutions that offer efficiency and comfort. But with comfort comes vulnerability; as critical infrastructure is more and more interconnected, the entry of a malicious actor in one system may have spillover effects to a wide range of sectors nationally and globally.
The digital attack surface is expanding at unprecedented levels, making preventive efforts extremely difficult. Today, any internet user makes up a potential entry and target for access to systems along complex supply chains. The gap between development and security is being utilised by hostile actors in cyberspace, ranging from lone actors to nations. China’s cyber groups are proving to use this gap, continuously conducting complex malicious cyber operations targeting international adversaries [source; source].
2.0. China’s Push for Global Power
China is pursuing a whole-of-government effort to spread its global influence. Through significant innovation and industrial policies, the country is increasingly trying to enable competitive military advances, seek independence from foreign technologies, and sustain economic growth. In its competitive relationship with the US, China is combining military, economic, technological, and diplomatic strategic goals pursuing intentional cooperation and securing what it perceives as a Chinese territory at the expense of US international influence.
China continuously expands its global influence through the Belt and Road Initiative (BRI). It almost explicitly targets Western research, technological, financial, and military sectors, utilising various tools from public investment to espionage and theft [source].
Offensive cyber capabilities constitute a crucial element in China’s push for global power. China’s ecosystem of APT actors, with substantial resources, presents prolific and influential espionage and is increasingly potentially a kinetic cyber threat. China’s APT network is launching cyber-attacks that could disrupt the opponent’s critical infrastructure. In addition, the country is coordinating large-scale cyber intrusions targeting civilian and non-civilian entities. Furthermore, cyber-espionage operations offer valuable opportunities for intelligence collection, attack, or influence operations. The country’s global intelligence footprint is expanding as China is utilising its cyber capabilities to support its growing global political, economic, and security interests.

3.0. China’s Cyber Capabilities: An Introduction
3.1. History
China’s interest in offensive capabilities in the digital environment began shortly after the Gulf War in 1995. The US swift victory in Iraq laid the foundation for a revolution in military affairs and the beginning of modern digital warfare capabilities by integrating information technology into its military strategy.
In 2003, Chinese operations in the digital environment became apparent. Code-named “Titan Rain”, US investigators traced several cyber espionage operations to computers in southern China. Researchers soon tracked the actors to the Chinese army. From that point, further incidents followed, all with the same objectives: espionage and theft of intellectual property. In 2013, the American cyber-intelligence firm Mandiant released a report assessing that the China-linked group APT1 had stolen hundreds of terabytes of data from at least 141 organisations since 2006 [source].
China’s APT ecosystem poses a substantial contemporary threat by reorganising its cyber policymaking institutions, developing sophisticated cyber capabilities, and perpetrating industrial-scale cyber espionage. China’s activities in cyberspace are highly stealthy and agile and bring potential kinetic effects to the target systems [source].
3.2. Chinese Cyber Doctrine: Information Operations
By spending the last few decades integrating offensive cyber capabilities into the broader operational concept of information operations, units within the People’s Liberation Army (PLA) are the primary coordinators and strategists of China’s offensive operations in cyberspace. According to PLA strategy, information operations constitute an element in which information is a domain and the central means to wage war. Hence, cyber operations are a crucial part of the modern battlefield. Together with electronic, space, and psychological warfare, it contributes to the concept of information operations.
In Chinese doctrine, the elements in information operations are coordinated as strategic weapons to disturb and sabotage an opponent’s system of systems. Victory is achieved by superior information advantage. It is centred on defending China’s ability to collect, use, and share such resources and denying its opponents’ abilities. Thus, cyber capabilities are a crucial part of China’s push for global power.
As a part of China’s extensive military reforms, the country established the PLA’s Strategic Support Force (SSF) in December 2015. SSF’s primary responsibility is cyber operations. The entity consists of two divisions: a Space Systems Department (SSD) and a Network Systems Department (NSD). The SSD focuses on space-related communications, computers, intelligence, surveillance, and reconnaissance. The NSD primarily focuses on cyber operations, electronic warfare, and psychological operations. In addition, both divisions are responsible for strategic intelligence and counter-space operations [source].
3.3. Common Motives
China’s main focus in cyberspace is espionage activities and theft. With the US as a primary competitor, China’s cyber operations mainly target sectors assessed to give China a competitive advantage [source]. Furthermore, Chinese APT groups utilise cyberattacks below the threshold of war intending to coerce rivals targeting government entities, multinational corporations and even small businesses [source].
4.0. China’s APT Ecosystem
4.1. APT1
First detected in 2006, APT1 has systematically conducted espionage activities, stealing hundreds of terabytes from at least 141 organisations. The group primarily focuses on Western targets and has been attributed to the Chinese military, namely the People’s Liberation Army (PLA) Unit 61398 (formerly of the 2nd Bureau of the PLA General Staff Department’s (GSD) 3rd Department), commonly known as Unit 61398 [source].
4.1.1. Known Alternative Names
Comment Crew, Comment Panda, PLA Unit 61398, TG-8223, BrownFox, Group 3, GIF89a, ShadyRAT, Shanghai Group, Byzantine Candor [source].
4.1.2. Targets
Target Sectors
- Information Technology
- Aerospace
- Public Administration
- Telecommunications
- Scientific Research
- Energy
- Transportation
- Financial
- Food and Agriculture
- Government
- Healthcare
- Media
- Mining
- Entertainment
[source]
Target Countries
- Belgium
- Canada
- France
- India
- Israel
- Japan
- Luxembourg
- Norway
- Singapore
- South Africa
- Switzerland
- Taiwan
- United Arab Emirates (UAE)
- United Kingdom (UK)
- US
[source]
4.1.3. Modus Operandi
The Modus Operandi (MO) of APT1 is sending spear phishing emails containing malicious code. The email information is often disguised in a text relevant to the recipient. APT1 also engages in creating webmail accounts using real people’s personal information. They also frequently use their own custom-made backdoors, enabling covert presence in protected systems. During their stay in each system, they usually install new backdoors allowing them continued access even after detection [source].
4.2. APT2
First observed in 2010, APT2 primarily conducts cyber operations aiming at intellectual property theft. The group is associated with PLA Unit 61486 (formerly of the 12th Bureau of the PLA’s 3rd General Staff Department). APT3 primarily conducts intelligence-gathering operations targeting government, defence, research, and technology sectors in the United States (US), specifically targeting the US defence and European satellite and aerospace industries [source; source]. According to cybersecurity firm Crowdstrike, the PLAs 3rd General Staff Department is generally acknowledged as China’s premier signals Intelligence (SIGINT) collection and analysis agency. The 12th Bureau Unit 61486, headquartered in Shanghai, supports China’s space surveillance network. [source].
4.2.1. Known Alternative Names
Putter Panda, MSUpdater [source].
4.2.2. Targets
Target Sectors
- Military
- Aerospace
4.2.3. Modus Operandi
The group is primarily given access through spear phishing emails tailored to the recipient. However, more in-depth information is minimal.
4.3. APT3
Labelled APT3 by the cybersecurity firm Mandiant, the group accounts for one of the more sophisticated threat actors within China’s broad APT network. Reportedly, the group has been active since 2010 and is being attributed to both China’s Ministry of State Security (MSS) and Chinese cybersecurity firm Guangzhou Boyu Information Technology Company, Ltd (“Boyusec”) [source]. Using zero-day exploits, APT3 is efficiently moving laterally between hosts and installing custom backdoors. Since June 2015, the group has shifted from primarily targeting US-based actors towards political organisations in Hong Kong [source; source].
The group frequently conducts sophisticated espionage operations sending malicious emails to steal sensitive information [source]. Prominent cyberespionage operations are Operation Clandestine Fox and Operation Double Tap [source].
4.3.1. Known Alternative Names
Gothic Panda, Pirpi, UPS Team, Buckeye, Threat Group-0110, TG-0110, Bronze Mayfair, Group 6 [source].
4.3.2. Targets
Target Sectors
- Aerospace
- Defence
- Construction
- Technology
- Transportation
- Telecommunication
Target Countries
- Belgium
- Hong Kong
- Italy
- Luxembourg
- Philippines
- Sweden
- UK
- US
- Vietnam
4.3.3. Modus Operandi
APT3 is utilising many tools, including phishing, spear phishing, zero-day exploits, and several unique and publicly available remote access tools. The phishing emails often sent by APT3 are usually generic and similar to common spam. Moreover, previous attacks have exploited an unpatched vulnerability in the Flash Video files of Adobe Flash Player [source].
4.4. APT4
Historically, APT4 is primarily targeting the US Defense Initial Base (DIB) on behalf of the Chinese government [source; source]. As a result, attacks on US DIB are conducted at a higher frequency than other commercial organisations. However, some open sources point to a focus shift as operations indicate an interest in the civil aviation sector. In addition, some sources make it unclear whether the group is still active [source; source].
4.4.1. Known Alternative Names
Samurai Panda, PLA Navy, Wisp Team, Maverick Panda, Sykipot, TG-0623, BRONZE EDISON [source].
4.4.2. Targets
Target Sectors
- Aerospace
- Defence
- Industrial engineering
- Electronics
- Automotive
- Government
- Telecommunication
- Transportation
4.4.3. Modus Operandi
APT4 sends spear phishing messages using the US government, Department of Defense (DoD), or defence industrial-related themes. The group tends to repurpose legitimate content within the message body from government or DoD websites [source].
4.5. APT5
Active since 2007 and associated with operating on behalf of the Chinese government [source], APT5 has been targeting organisations across multiple industries in the US, Europe, and Asia but is focusing on telecommunications and technology in Southeast Asia. Observed filenames detected during recent attacks indicate an interest in product specifications, emails concerning technical information, procurement bids and proposals, and information regarding unmanned aerial vehicles (UAVs). The group is assessed to consist of several subgroups, often with their own tactics and structure [source].
4.5.1. Known Alternative Names
DPD, Keyhole Panda, Poisoned Flight, TG-2754, Tools Binanen, Comfoo, Gh0st RAT, Isastart, Leouncia, OrcaRAT, PcShare, Skeleton Key, SlyPidgin, VinSelf, TEMP.Bottle, Bronze Fleetwood [source; source].
4.5.2. Targets
Target Sectors
- Asia-based telecommunication
- High-tech
- Military tech
4.5.3. Modus Operandi
As mentioned, APT5 consists of several subgroups with their own tactics and structure. However, APT5 is known to primarily use malware with keylogging capabilities, specifically targeting telecommunication companies. In addition, the group has been observed to show a significant interest in compromising networking devices and changing their underlying software [source].
4.6. APT 6
Believed to have been active since at least 2008, APT6 primarily engages in data theft on behalf of the Chinese government [source], targeting the organisation’s competitive data and projects. Known attacks have mainly targeted US and UK governments and companies in the transportation, automotive, construction, engineering, telecommunications, electronic, construction, and materials sectors for valuable data [source]. In 2016, the Federal Bureau of Investigation (FBI) issued an alert about an ongoing cyber campaign that had compromised and stolen data from numerous government and commercial networks over five years. The attack was later attributed to APT6 [source].
4.6.1. Known Alternative Names
1.php group
4.6.2. Targets
Target Sectors
- Transportation
- Automotive
- Construction and Engineering
- Telecommunication
Target Countries
- US
- UK
4.6.3. Modus Operandi
APT6 is known for utilising a broad range of custom backdoors, including those used by other APT groups as backdoors unique to the group. However, the FBI 2016 alert indicated the ability to maintain a presence in compromised networks after detection [source].
4.7. APT 7
APT7 is primarily focusing on the theft of intellectual property. However, like several other APT groups, the targets are often data and projects that make an organisation competitive. Unfortunately, very little information is publicly available about this group.
4.7.1 Targets
Target Sectors
- Construction
- Engineering
- Aerospace
- Defence
Target Countries
- US
- UK
4.7.2. Modus Operandi
APT7 primarily targets the digital supply chain to enable access to a specific organisation [source].
4.8. APT 8/20
APT8 (or APT20) primarily focuses on data theft. The group has been observed to focus on intellectual property theft and monitoring individuals’ activities for ideological reasons. The group is assessed to act as freelancers with some sponsorship from the Chinese government [source].
4.8.1. Known Alternative Names
Violin Panda, TH3Bug, Twivy [source].
4.8.2. Targets
Target Sectors
- Aviation
- Construction
- Defence
- Energy
- Engineering
- Financial
- Government
- Healthcare
- Telecommunication
- Transportation
- Uyghur sympathisers
Target Countries
- US
- Germany
- UK
- India
- Japan
- Brazil
- China
- France
- Italy
- Mexico
- Portugal
- Spain
- Thailand
4.8.3. Modus Operandi
APT8/20 is known to use spear phishing emails or to exploit vulnerable internet-facing web servers to gain access to target actors’ systems. Moreover, the group uses strategic web compromises to increase their scope of potential targets using the information on what users visit that specific webpage. Hence, the group is compromising websites their intended targets are likely to visit, such as Uyghur websites and so-called water hole attacks.
4.9. APT 9
Like many other groups, APT9 engages in cyber operations where the goal is data theft with some degree of state sponsorship. The group primarily focuses on competitive data and projects from organisations within the healthcare, pharmaceuticals, construction, engineering, aerospace, and defence industries. The group shares some similarities with APT10 [source].
4.9.1. Known Alternative Names
Group 27, FlowerLady, FlowerShow, Nightshade Panda [source].
4.9.2. Targets
Target Sectors
- Health care
- Pharmaceuticals
- Construction
- Engineering
- Aerospace
- Defence
4.9.3. Modus Operandi
APT9 has been observed to use a variety of spear phishing campaigns, using valid accounts and remote services for Initial Access to target companies within the pharmaceuticals and biotechnology industry. Furthermore, the group uses publicly available as well as custom-made backdoors.
4.10. APT10
Identified in 2006 [source], APT10 primarily targets aerospace, telecommunication, and government services in Japan, the US, and Europe. The group is believed to operate to support Chinese national security goals. It is associated with the Tianjin bureau of the MSS. Furthermore, there are indications of APT10 operating to support Chinese corporations acquiring military and intelligence information and confidential business data.
APT10 perpetrated Operation Cloud Hopper, a global cyberespionage campaign that compromised several managed service providers in the United States and other countries to obtain the information of their clients in the engineering, industrial manufacturing, retail, energy, pharmaceuticals, telecommunications, and government industries. According to cybersecurity firm Symantec in April 2022, the group targets government-related institutions and nongovernmental organisations in North America, the Middle East, and Europe [source; source; source].

4.10.1. Known Alternative Names
HOGFISH, Cicada, Cloud Hopper, Red Apollo, CNVX, Stone Panda, MenuPass, and POTASSIUM. Believed to be a part of the Tianjin bureau of the Chinese Ministry of State Security [source; source].
4.10.2. Targets
Target Sectors
- Construction
- Engineering
- Aerospace
- Telecommunication
- Government
Target Countries
- US
- Japan
- Europe
4.10.3. Modus Operandi
APT10 uses traditional spear phishing techniques and managed service providers to access targets’ networks.
4.11. APT 12
APT12 is attributed to be operating on behalf of the Chinese PLA. The group targets various victims that are assessed to be consistent with the Chinese government’s larger strategic goals, primarily but not limited to journalists, governments, and the defence sector in Japan and Taiwan. For example, in 2012, the group hacked the New York Times [source].
4.11.1. Known Alternative Names
Numbered Panda, TG-2754, BeeBus, Galc Team, DynCALC, DyncCalc, DNSCalc, Group 22, Crimson Iron. IXESHE, JOYRAT, DN- SCALC, BRONZE GLOBE [source; source].
4.11.2. Targets
Target Sectors
- Defence
- Electronics
- Government
- Media
- Telecommunications
- Journalists
Target Countries
- Japan
- Taiwan
- Germany
- US
4.11.3. Modus Operandi
APT12 is observed to deliver documents, including malicious code, via phishing emails from valid but compromised accounts. Moreover, the group is known to dynamically calculate Command and Control (C2) ports by resolving a DNS. The method allows the group to bypass egress filtering implemented to prevent unauthorised communications.
4.12. APT 14
Active since 2013 and associated with the PLA Navy [source; source], APT14 engages in cyber operations where the goal is data theft, with a possible focus on military and maritime equipment, operations, and policies. The stolen data, especially encryption and satellite communication equipment specifications, is likely gathered to enhance military operations, such as intercepting signals or interfering with military satellite communication networks [source]. Cybersecurity firm CrowdStrike notes that APT14 has heavily targeted companies in the United States, Germany, Sweden, the UK, and Australia that provide maritime satellite systems, aerospace companies, and defence contractors [source].
4.12.1. Known Alternative Names
Anchor Panda
4.12.2. Targets
Target Sectors
- Aerospace
- Defence
- Engineering
- Government
Target Countries
- Australia
- Germany
- Sweden
- UK
- US
4.12.3. Modus Operandi
APT14 does not usually use zero-day exploits but tends to leverage exploits once they are made public. In addition, the group often uses spear-phishing techniques that appear to originate from valid organisations.
4.13. APT 15/25
Since at least 2010, APT15 (or APT25) targets a wide variety of organisations primarily based in Europe, the US, and South Africa, focusing on data theft. The group is often sharing resources with other known APTs making attribution challenging. Moreover, the group’s targets are often interlinked with those of interest to the Chinese government. They are potentially associated with the Chinese defence contractor Xi’an Tianhe Defense Technology [source]. According to cybersecurity researchers at Palo Alto, APT15/25 is behind a new series of attacks targeting the Iranian government between July and December 2022 [source].
4.13.1. Known Alternative Names
NICKEL, KeChang, Ke3ChangVixen Panda, Playful Taurus, BackdoorDiplomacy, Mirage, Playful Dragon, Metushy, Lurid, Social Network Team, Royal APT, BRONZE PALACE, BRONZE DAVENPORT, BRONZE IDLEWOOD, G0004, Red Vulture [source; source; source].
4.13.2. Targets
Target Sectors
- Defence
- Financial
- Energy
- Military
- Media
- Transportation
Target Countries
- US
- South Africa
- Europe
4.13.3. Modus Operandi
APT15/25 typically uses sophisticated spear phishing emails for initial compromise against targets of interest to the Chinese government. To avoid attribution, the group typically does not use zero-day exploits. Still, it may leverage those exploits once they are public.
4.14. APT 16
APT16 primarily targets Japanese and Taiwanese organisations within the political and journalistic sphere. The group also focuses on data theft within the finance and governmental sectors.
4.14.1. Known Alternative Names
SVCMONDR
4.14.2. Targets
Target Sectors
- Financial
- Government
- Media
Target Countries
- Japan
- Taiwan
- Thailand
4.14.3. Modus Operandi
APT16 is known to use spear phishing emails targeting Japanese and Taiwanese media organisations. In addition, known methods have been luring users to register on a Taiwanese auction site and delivering malicious Microsoft Word documents.
4.15. APT 17
APT17 is known to conduct intrusions targeting US government entities, the aerospace and defence industry, government, and financial and mining companies. The group uses an unlimited number of zero-day exploits, mainly focusing on the digital supply chain of larger organisations. Moreover, the group is efficiently utilising water hole attacks, intending to compromise certain websites that are likely to be visited by target organisations. Apart from APT17 access to zero days, the usual scale of attacks is a prime indicator of the group’s resources. Victims are rarely attacked for crime or theft but for the wholesale gathering of intellectual property and valuable intelligence. The group is undoubtedly supported by a nation-state and has been attributed to the Chinese government and the MSS [source; source].
4.15.1. Known Alternative Names
Tailgater Team, Elderwood, Elderwood Gang, Sneaky Panda, SIG22, Beijing Group, TEMP.Avengers, Dogfish, Deputy Dog, ATK 2, Hidden Lynx, Aurora Panda, Hidden Lynx, Tailgater Team, Group 8, Axiom, SportsFans.
4.15.2. Targets
Target Sectors
- Government
- Defence
- Aerospace
- Energy
- Education
- Financial
- Media
- Mining
Target Countries
- Belgium
- China
- Germany
- Indonesia
- Italy
- Japan
- Netherlands
- Switzerland
- Russia
- UK
- US
4.15.3. Modus Operandi
APT17 is known for repeatedly conducting large-scale attacks using unique zero-day exploits. Furthermore, the group efficiently creates profiles on different forums to spread its used malware, making attribution challenging.
4.16. APT 18
Active since at least 2009 and reportedly associated with the PLA Navy, APT18 primarily conducts espionage operations targeting US industries, including manufacturing, technology, government, healthcare, defence, telecommunications, and human rights groups. The group distinguishes itself for delivering recently released exploits shortly after they are public [source; source].
4.16.1. Known Alternative Names
Dynamite Panda, TG-0416, Wekby, Scandium, TA428 [source].
4.16.2. Targets
Target Sectors
- Aerospace
- Defence
- Construction
- Education
- Healthcare
- Telecommunication
- Transportation
Target Countries
- US
4.16.3. Modus Operandi
APT18 tends to use zero-day exploits very shortly after they are made public. Furthermore, the group stands out for its shift in resources, i.e., selection of targets, preparation of infrastructure, and updating tools. Finally, the capability of adaptation allows the group to take advantage of highly unexpected opportunities swiftly.
4.17. APT 19/26
APT19 is likely the same group as APT26. The group primarily conducts intellectual property theft targeting US and Australian organisations in the defence, finance, energy, pharmaceutical, telecommunications, high-tech, education, manufacturing, legal and investment sectors. Assessments regarding attribution differ among researchers. However, there are some indications that APT19/26 is composed of freelancers with some degree of sponsorship by the Chinese government, and some points toward direct affiliation with the MSS. Moreover, there are indications of links to APT10 [source; source; source].
4.17.1. Known Alternative Names
Shell Crew, WebMasters, KungFu Kittens, Group 13, PinkPanther, Black Vine, Deep Panda, SportsFans, Turbine Panda, C0d0s0, Pupa, BRONZE FIRESTONE, Codoso Team, G0009, G0073, Pupa, and Sunshop Group [source; source; source].
4.17.2. Targets
Target Sectors
- Aerospace
- Aviation
- Defence
- Finance
- Food and Agriculture
- Education
- Energy
- Government
- Healthcare
- Pharmaceutical
- Telecommunication
- Political dissidents
Target Countries
- Australia
- Canada
- China
- Denmark
- France
- Germany
- India
- Italy
- UK
- US
4.17.3. Modus Operandi
The group frequently uses phishing techniques and strategic web compromises to enable access to networks. Furthermore, once inside a victim environment, APT19/26 customise backdoors to secure its presence.
4.18. APT 21
APT21 leverages attachments themed on national security issues in the Russian language. The group targets government entities and dissident political groups utilising social engineering techniques. In addition, APT21 is suspected of conducting a global cyber-espionage campaign using the NetTraveler tool and has reportedly been targeting over 350 victims in 40 countries. Furthermore, according to cybersecurity firm Crowdstrike, APT21 likely originates from PLAs first Technical Reconnaissance Bureau in the former Lanzhou Military Region. It may be a part of the SSF [source].
4.18.1. Known Alternative Names
Hammer Panda, TEMP.Zhenbao.
4.18.2. Targets
Target Sectors
- Defence
- Government
- Energy
- Political dissidents (mainly Tibet and Xinjiang)
Target Countries
- Afghanistan
- Australia
- Austria
- Bangladesh
- Belarus
- Belgium
- Cambodia
- Canada
- Chile
- China
- Germany
- Greece
- Hong Kong
- India
- Indonesia
- Iran
- Japan
- Jordan
- Kazakhstan
- Kyrgyzstan
- Lithuania
- Malaysia
- Mongolia
- Morocco
- Nepal
- Pakistan
- Qatar
- Russia
- Slovenia
- South Korea
- Spain
- Suriname
- Syria
- Tajikistan
- Thailand
- Turkey
- Turkmenistan
- UK
- Ukraine
- US
- Uzbekistan
4.18.3. Modus Operandi
APT21 often leverages spear phishing emails with malicious attachments or links to malicious files or websites. Furthermore, the group is using strategic web compromises when targeting potential victims. Most significantly, APT21 tends to use its customised backdoors, avoiding publicly available tools.
4.19. APT 22
Active since at least 2014, APT22 is believed to have a nexus to China. The group primarily carries out attacks and intrusions targeting public and private sector entities, including dissidents in East Asia, Europe, and the United States. According to Secureworks, APT22 conducted a long-running espionage campaign against the Indian government and commercial organisations between 2014 and 2015 [source; source].
4.19.1. Known Alternative Names
Barista, BRONZE OLIVE, Wet Panda [source; source].
4.19.2. Targets
Target Sectors
- Healthcare
- Pharmaceutical
- Military
- Finance
Target Countries
- US
- India
4.19.3. Modus Operandi
APT22 is using strategic web compromises to exploit targets of interest passively. Moreover, the group is known to identify vulnerable public-facing web servers on victim networks and upload web shells to gain access to the victim network [source].
4.20. APT 23
Rather than intellectual property, APT23 focuses on information of political and military significance. Hence, the group performs data theft in support of more traditional espionage operations [source]. For example, cybersecurity firm Anomali reported in 2020 that APT23 conducted spear-phishing campaigns targeting Vietnamese government officials near the disputed Paracel Islands in the South China Sea [source].
4.20.1. Known Alternative Names
Pirate Panda, KeyBoy, Tropic Trooper, BRONZE HOBART, G0081 [source].
4.20.2. Targets
Target Sectors
- Government
- Media
- Military
Target Countries
- Philippines
- US
4.20.3. Modus Operandi
APT23 utilises spear phishing techniques to gain access to victim networks. The group is not known to use zero-day exploits but has leveraged such exploits once public.
4.21. APT 24
Likely active since at least 2008, APT24 is known for targeting organisations in the government, healthcare, construction and engineering, mining, nonprofit, and telecommunications sectors in the US and Taiwan. In addition, the group focuses on data theft, mainly documents of political significance, indicating an interest in monitoring regional nation-states on issues applicable to China’s ongoing territorial or sovereignty dispute [source; source].
4.21.1. Known Alternative Names
PittyTiger
4.21.2. Targets
Target Sectors
- Healthcare
- Government
- Engineering
- Mining
- Telecommunications
Target Countries
- Taiwan
- US
4.21.3. Modus Operandi
APT24 is using the military, energy, or business strategy-themed phishing emails. Moreover, APT24 engages in intellectual property theft, usually focusing on the data and projects that make a particular organisation competitive. Furthermore, the group has been seen using Microsoft Office products to obtain legitimate credentials and the RAR archive utility to encrypt and compress stolen data before transferring it out of the network [source].
4.22. APT27
Active since at least 2009, APT27 is known to extensively use strategic web compromises when targeting victims, primarily within aerospace and transport. Moreover, the group is using watering holes and spear phishing attacks. Although the main goal is intellectual property theft, the group is moving towards financially motivated attacks, including ransomware in its offensive campaigns [source]. The Chinese government is likely sponsoring the group in executing multiple long-term, highly targeted attacks against organisations in the defence, technology, energy, and manufacturing sectors [source].
4.22.1. Known Alternative Names
Threat Group-3390, Emissary Panda, LuckyMouse, Bronze Union, TEMP.Hippo, Group 35, ATK 15, ZipToken Budworm, Iron Tiger, IronPanda [source; source].
4.22.2. Targets
Target Sectors
- Aerospace
- Aviation
- Defence
- Education
- Finance
- Government
- Technology
- Telecommunications
Target Countries
- Australia
- Canada
- China
- Hong Kong
- India
- Iran
- Israel
- Japan
- Philippines
- Russia
- Spain
- South Korea
- Taiwan
- Thailand
- Tibet
- Turkey
- UK
- US
[source]
4.22.3. Modus Operandi
APT27 is primarily using spear phishing as a method for initial compromise. The group has been observed to use compromised accounts when sending spear phishing emails. However, APT27 is not known for using original zero-day exploits but may leverage those exploits once public. Additionally, APT27 may compromise vulnerable web applications to gain an initial foothold. Standard methods are watering hole attacks, remote code execution and supply chain attacks [source].
4.23. APT30
Active since at least 2005, APT30 is distinguished not only for sustained activity over a long time but also for conducting successful operations despite its continuous methods. The group is known for modifying and adapting source code to maintain the same tools, tactics, and infrastructure over time. The group is associated with the Chinese government. It is assessed to prioritise targets and develop malware from a coherent plan in a collaborative environment. Its members are most likely working in shifts. Since at least 2005, APT30 has been capable of infecting air-gapped networks.
The group has yet to be observed to target credit card data or bank transfer credentials, i.e., data that can be readily monetised. Instead, its tools focus on data theft. They include functionality that enables APT30 to identify and steal information. APT30’s primary interest lies in ASEAN-linked organisations and governments, specifically journalists reporting on issues linked to the Chinese Communist Party [source].
Assessments differ on whether APT30 is the infamous APT group Naikon [source; source; source]. First detected in 2010, the group under the alias Naikon is associated with the PLA Unit 78020 that operates in the Southern Theater Command’s area of responsibility and currently focuses on military and government targets in Southeast Asia and does hence share similarities with APT30 [source; source].
4.23.1. Known Alternative Names
Override Panda, Naikon, Lotus Panda [source; source].
4.23.2. Targets
Target Sectors
- Defence
- Government
Target Countries
- Bhutan
- Brunei
- Cambodia
- India
- Indonesia
- Japan
- Laos
- Malaysia
- Myanmar
- Nepal
- Philippines
- Saudi Arabia
- Singapore
- South Korea
- Thailand
- Vietnam
- US
4.23.3. Modus Operandi
APT30 uses a broad tool kit including downloaders, backdoors, a central controller and several components designed to infect removable drives and cross-air-gapped networks to steal data. Moreover, APT30 frequently registers its DNS domains for malware CnC activities [source].
4.24. APT31
Associated with the MSS, APT31 is mainly focusing on cyber espionage activities targeting government, financial, and defence organisations. In addition, it focuses on obtaining information of potential value to the Chinese government and state-owned enterprises intended to increase political, economic, and military advantages. In March 2022, Google’s Threat Analysis Group warned Gmail users associated with the US government that APT31 conducted phishing attacks targeting their accounts [source].
4.24.1. Known Alternative Names
Judgment Panda, Zirconium, Hurricane Panda, BRONZE VINEWOOD, Black Vine, TEMP.Avengers, Red Keres [source; source].
4.24.2. Targets
Target Sectors
- Aerospace
- Agriculture
- Defence
- Government
- Finance
- Healthcare
- Energy
- Technology
Target Countries
- Japan
- US
- UK
- India
- Canada
- Brazil
- South Africa
- Australia
- Thailand
- South Korea
- France
- Switzerland
- Sweden
- Finland
- Norway
4.24.3. Modus Operandi
APT31 is mainly focusing on theft as opposed to financial gain. However, the group has exploited vulnerabilities in applications such as Java and Adobe Flash to compromise victim environments.
4.25. APT40
Since at least 2009, APT40 has been a state-sponsored espionage actor believed to be a force multiplier in China’s efforts to modernise its naval capabilities. The group is known for targeting wide-scale research projects at universities and obtaining designs for marine equipment and vehicles [source]. In addition, the group’s operations usually target government-sponsored projects, including large amounts of project-specific information. Such information includes proposals, financial data, shipping information, plans, drawings, and raw data. Furthermore, in addition to its maritime focus, APT conducts espionage campaigns targeting traditional intelligence targets with operations in Southeast Asia. To summarise, targets are often strategically crucial to China’s BRI and include Cambodia, Belgium, Germany, Hong Kong, Philippines, Malaysia, Norway, Saudi Arabia, Switzerland, the United States, and the United Kingdom [source].
4.25.1. Known Alternative Names
BRONZE MOHAWK, FEVERDREAM, G0065, Gadolinium, GreenCrash, Hellsing, Kryptonite Panda, Leviathan, MUDCARP, Periscope, Temp.Periscope, Temp.Jumper [source; source].
4.25.2. Targets
Target Sectors
- Government
- Education
- Biomedical
- Robotics
- Maritime research
Target Countries
- US
- Canada
- BRI-countries’ industries
[source]
4.25.3. Modus Operandi
APT40 is usually disguised as a prominent actor of probable interest to a target from which spear phishing emails are sent. Typical tactics are pretending to be a journalist, an individual representing a significant publication, or someone from a relevant military organisation. Furthermore, APT40 is using compromised email accounts for spear phishing purposes.
4.26. APT41
Since at least 2012, APT41 has been a prolific actor affiliated with the MSS carrying out Chinese state-sponsored espionage activities. In addition, the group is known to conduct financially motivated attacks potentially beyond state control. For example, until 2014, the group usually conducted attacks targeting video game industries. However, APT41 has been balancing espionage activities with financially motivated operations, which is remarkable among Chinese-sponsored APTs. Furthermore, the group shares tools and digital certificates with other APTs, which makes attribution challenging. Moreover, APT41 is known to manipulate virtual currencies and track individuals [source; source].
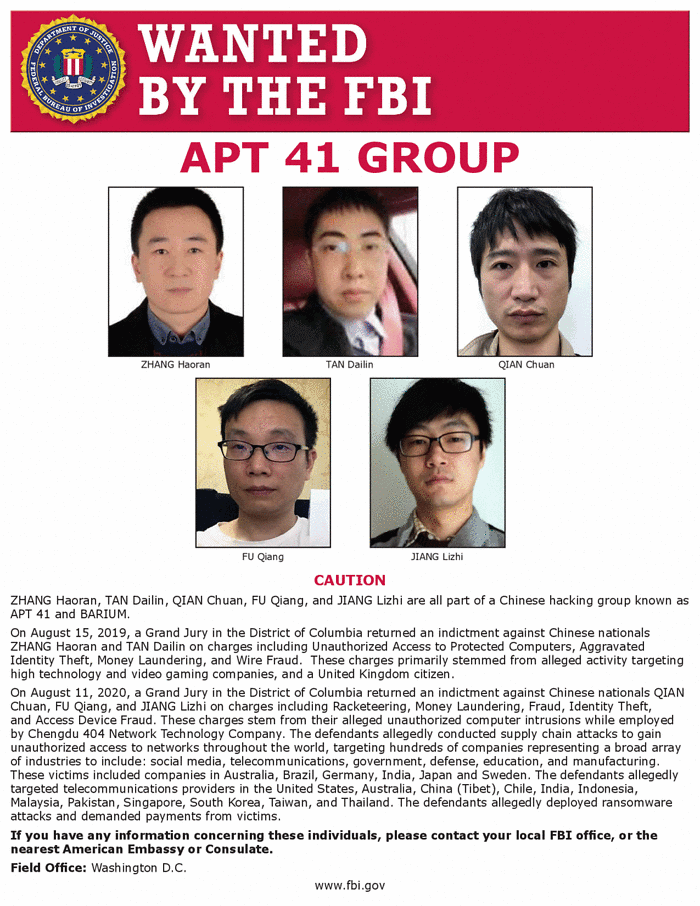
4.26.1. Known Alternative Names
Double Dragon, Barium, Winnti, Wicked Panda, Wicked Spider, TG-2633, Bronze Atlas, Red Kelpie [source; source].
4.26.2. Targets
Target sectors
- Construction
- Defence
- Education
- Entertainment
- Energy
- Financial
- Government
- Healthcare
- Energy
- Media
- Pharmaceutical
- Telecommunication
- Transport
Target Countries
- Australia
- Brazil
- Canada
- Chile
- Denmark
- Finland
- France
- Germany
- Hong Kong
- India
- Indonesia
- Italy
- Japan
- Malaysia
- Mexico
- Myanmar
- Netherlands
- Pakistan
- Philippines
- Poland
- Qatar
- Saudi Arabia
- Singapore
- South Korea
- Sweden
- Switzerland
- Taiwan
- Thailand
- Turkey
- UAE
- UK
- US
4.26.3. Modus Operandi
APT41 often uses spear-phishing emails with attachments such as compiled HTML files for initial compromise. However, when enabled access, APT41 is known to leverage more sophisticated TTP, deploying additional malicious code. For example, in a single one-year-long campaign, APT41 launched 150 unique pieces of malware, including backdoors, credential stealers, keyloggers, and rootkits.
5.0. Assessing the threat: Some Concluding Thoughts
China possesses substantial offensive cyber capabilities and presents a growing threat. When looking at the ecosystem of hostile actors, attacks can and will cause minor to large-scale disruptions worldwide serving Chinese foreign policy objectives.
As target sectors become more interconnected and geostrategic competition intensifies, Chinese APT actors will likely continue to increase their capabilities and enhance the threat towards its opponents. Russia’s invasion of Ukraine may influence the focus of Russian cyber operations, limiting them to Ukraine and European actors. Such a development may provide an increased attack surface for Chinese malicious activities reaching beyond current strategic objectives. Furthermore, the ongoing tensions in Asia with the US support of Japan and South Korea’s reactions to recent North Korean missile launches may constitute a perceived threat and hence bring incentives for increasing focus on the US activities in the region and beyond.
Western countries will likely remain an appealing target for espionage targeting industrial services, government, health care, energy, and education sectors. Furthermore, there will probably be an increase in supply-chain attacks to broaden the attack surface further and circumvent targets’ security protocols. Moreover, it is reasonable to believe that Chinese APT groups will follow the Modus Operandi of APT27 and APT41, i.e., including ransomware attacks in their offensive portfolio, broadening it from mere espionage. Although, on the one hand, ransomware attacks will offer financial muscles in times of economic uncertainty, on the other hand, they will make attribution even more challenging as the motives behind the attacks are blurred.
When looking at China’s global aspirations, it is evident that geopolitics constitutes and will remain a key driver for developing offensive cyber capabilities. Groups operating under the MSS and SSF will likely continue to conduct hostile intelligence activities targeting the opponent’s systems. Furthermore, China will likely enhance their efforts in slowing down an American response to regional operations, especially targeting Taiwan. As the US constitutes China’s main competitor, it is reasonable to assume that Chinese APT actors coordinated by the MSS and SSF will try to undermine internal and external confidence in American cyber capabilities.
Moreover, the Arctic region is developing into a hotbed for future competition and potential conflict, most recently as Sweden discovered Europe’s most significant assets of critical minerals essential for green transitions. With increasing transport routes due to climate change, such a development will likely continue attracting Chinese foreign policy interests and increase the range of cyber targets.

